Your Router Is Watching You: The Dark Side of Wi-Fi Sensing Technology
4 September 2025 - Reading time: 7 minutes
Have you ever wondered whether your humble Wi-Fi router could, by any chance, tell you who entered your living room, when they moved or even what they were doing? That question is no longer theoretical. It all becomes a reality thanks to the Wi-Fi Sensing technology. While the idea sounds like something out of science fiction, many of today’s routers are already capable of turning into motion detectors and more.
How does the magic work?
At its core, Wi-Fi Sensing relies on beamforming technology: a clever method employed by the majority of modern routers that enables them to focus their signals on specific devices while communicating with them. We are talking about routers equipped with multiple antennas and capable of supporting at least the 802.11ac version (also referred to as “Wi-Fi Five”). Beamforming generally results in faster and stronger signal quality, which we've all come to rely on when browsing the Internet, streaming our favourite movies or playing online games. But this is only a part of the story.
In our modern houses, every device - your smart speaker, TV or printer - is quietly and constantly emitting radio waves. When these signals bounce off objects and people, they change subtly. Modern routers equipped with beamforming focus their antennas to maximise signal strength towards each device, constantly measuring the Channel State Information (CSI) - the amplitude and phase of the transmitted radio waves.
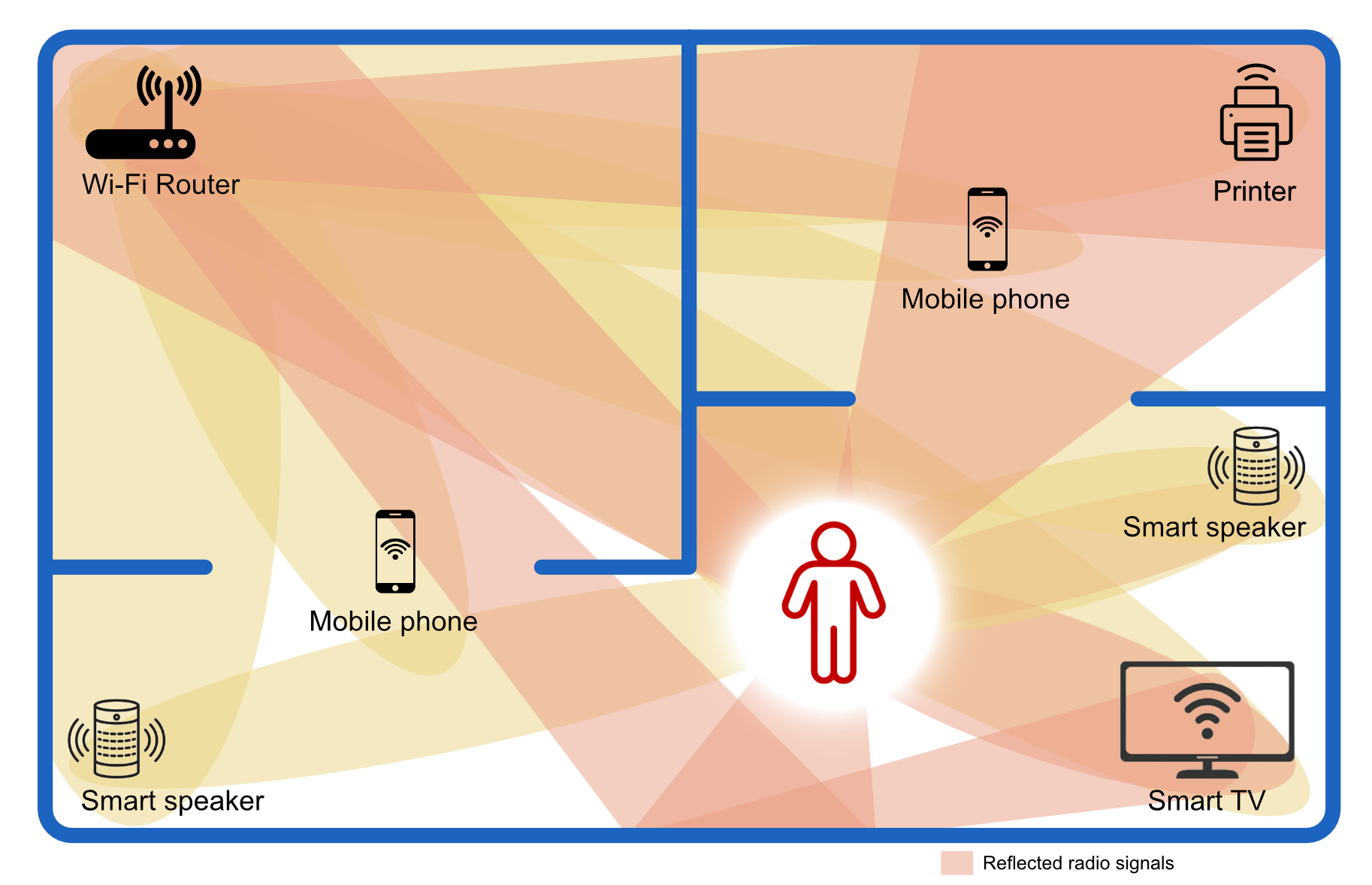
When a person walks between the router and one of its connected devices, that human body introduces tiny changes in the pattern of radio waves. The router detects these deviations as shifts in CSI. By feeding those patterns to machine learning algorithms, it is possible to recognise movement, detect an intrusion, or even infer specific actions such as standing up or waving a hand. All this happens at the very edge of the network - inside the router itself - so no extra hardware is required beyond what most households already have. What begins with just detecting motion eventually becomes a highly accurate system that can tell where you are at different times of day, in which particular room, and how many people were with you. Wi-Fi Sensing is capable of detecting with high accuracy (and leaking!) users’ personal characteristics such as height, weight, or gender, thereby breaching privacy regulatory frameworks.
Implications
Many could welcome Wi-Fi sensing into their lives for its convenience, as “yet another smart home feature” like lights could be switched on when a user walks through the door and have them to automatically switch off once they leave. What's not to like: you have a home surveillance system for free.
However, as it stands now, users are unaware that these new innovations can easily introduce security threats to their very own homes. When used by malicious individuals or exploited, Wi-Fi sensing can be misused and pose as a serious threat to personal or corporate security and privacy, exposing even the most seemingly secure of living environments.
Not only can homeowners monitor who comes and goes. Vendors can easily share the collected motion or presence-related data with police or other “third parties” on demand. The collected information can also be sold or stolen, revealing the life patterns of thousands of homeowners.
We should not forget that home routers are already frequent targets for hackers who either eavesdrop on users or profit from the collected data in various ways. Nothing stops malicious actors from “mining” motion sensor data and, e.g. selling those insights to burglars or “whoever pays”.
Fun fact: it might be interesting to know that IEEE 802.11bf standard will be ready to formally standardise Wi Fi sensing in 2025. The amendment adds MAC and PHY layers features that enable robust sensing in both sub 7 GHz bands and frequencies above 45 GHz. When published, 802.11bf provides a unified framework for presence detection, recognition of human activities, and monitoring the environment by using existing Wi Fi infrastructure. So there will be more Wi-Fi Sensing everywhere, and we all have to understand well the security implications of this technology.
Can We Protect Ourselves?
Protecting yourself against these types of vulnerabilities is more crucial than you think. You have no influence on anything that happens on the vendor’s side, but you certainly have control over what happens in your home or office. Because Wi-Fi sensing relies on the standard wireless signals that already fill our environment, it’s nearly impossible to block it entirely. However, you can still reduce its potential dangers by shielding critical spaces from the wireless signals. In highly sensitive areas, such as research labs or conference rooms, take care to block Wi-Fi entirely. Proper signal shielding will neutralise attacks that depend on Wi Fi Sensing. If you want to go one step further, consider installing structural barriers such as Faraday cages or using materials that absorb or reflect radio waves, or otherwise preventing the signals from leaking into or out of those spaces.
Don’t forget about the elements of standard cyber hygiene. Make sure all Wi-Fi-enabled smart devices within your network are properly patched, their software up-to-date, and that a strict WPA2 or WPA3 security is in place. If possible, avoid sharing passwords with people outside of your “circle of trust” (personal or corporate) who, sometimes, have little understanding of security. Using guest Wi-Fi passwords with expiration time could be a good idea. One more thing that is worth remembering: think twice before introducing a new device to your home or corporate Wi-Fi network, especially if the vendor is, let’s call it “questionable”. I would also strongly recommend avoiding registrations with the vendor’s cloud services, unless it is absolutely necessary and you understand all the implications. If you have no choice and must register, use a disposable email address for registration and do not provide any of your personal details (yes, I am talking about security cameras, cleaning robots, etc.).
Finally, always stay proactive: monitor your network for anomalies, keep up to date with emerging risks, and remember that having even the simple measures in place, like regular updates, strong keys, and cautious onboarding, is better than doing nothing.
More Information
- A large collection of Wi-Fi Sensing Resources (https://www.wifisensing.io)
- ESPARGOS is a very large dataset (~120 GB https://espargos.net) available if you want to conduct your own research. The dataset was created with a phase-locked antenna array and allows studying spatial problems such as positioning, segmentation and phase effects.