The Price of Neglect. The Big Questions Behind Jaguar Land Rover’s Government £1.5 B Cyber Bailout.
4 October 2025 - Reading time: 9 minutes
When a cyber attack stops Britain’s most iconic carmaker, the government steps in with a surprising loan guarantee that would make even the most cautious CFO blush.
The Great British Stall or “JLR on Full Brakes”
Picture this: it’s September 1st 2025, and the Jaguar Land Rover (JLR) production lines have gone silent across Solihull, Wolverhampton, and Halewood. A massive cyberattack - conducted by a gang called Scattered Lapsus$ Hunters has taken JLR’s production lines hostage for almost a month. The result? Roughly £50 million is lost per week, and the whole supply chain is on the brink of bankruptcy.
In the midst of this disaster, we saw a truly unprecedented move: the UK government “pulling a rabbit out of a hat” and rolling out a whopping £1.5 billion loan guarantee to keep the wheels turning. Yes, it sounds like a lifeline for the UK’s iconic carmaker, but it raises a pile of disturbing questions: Why on earth should UK taxpayers chip in for a private company that clearly didn’t pay enough attention to its cybersecurity? Will this set a dangerous precedent, allowing big firms to afford paying even less attention to cybersecurity because now they know the government will help them out? Let’s find out!
The Government’s Spin: “Guys, We Are Protecting Jobs”
It’s the first time a UK company has received financial support specifically because of a cyber incident. But is it an entirely good thing?
Business Secretary Peter Kyle declared that the loan is about safeguarding livelihoods across the West Midlands and beyond. He painted JLR as an exemplary pillar of modern UK manufacturing, supporting over 800,000 jobs nationwide. Fair enough.
Now let’s put our sceptical hats on for a moment. JLR is not a struggling startup, right? It’s a giant business with 34,000 direct UK employees and an enormous supply chain that employs more than 120,000 people. So why does the government feel compelled to guarantee a loan? The answer is twofold:
- Prevent supply chain “ripple effect”: JLR’s 700 suppliers are mostly SMEs. A month of halted production means they’re staring at possible bankruptcy. That’s clearly bad.
- National pride: Jaguar Land Rover is an icon; it’s the “J” in Britain’s automotive DNA.
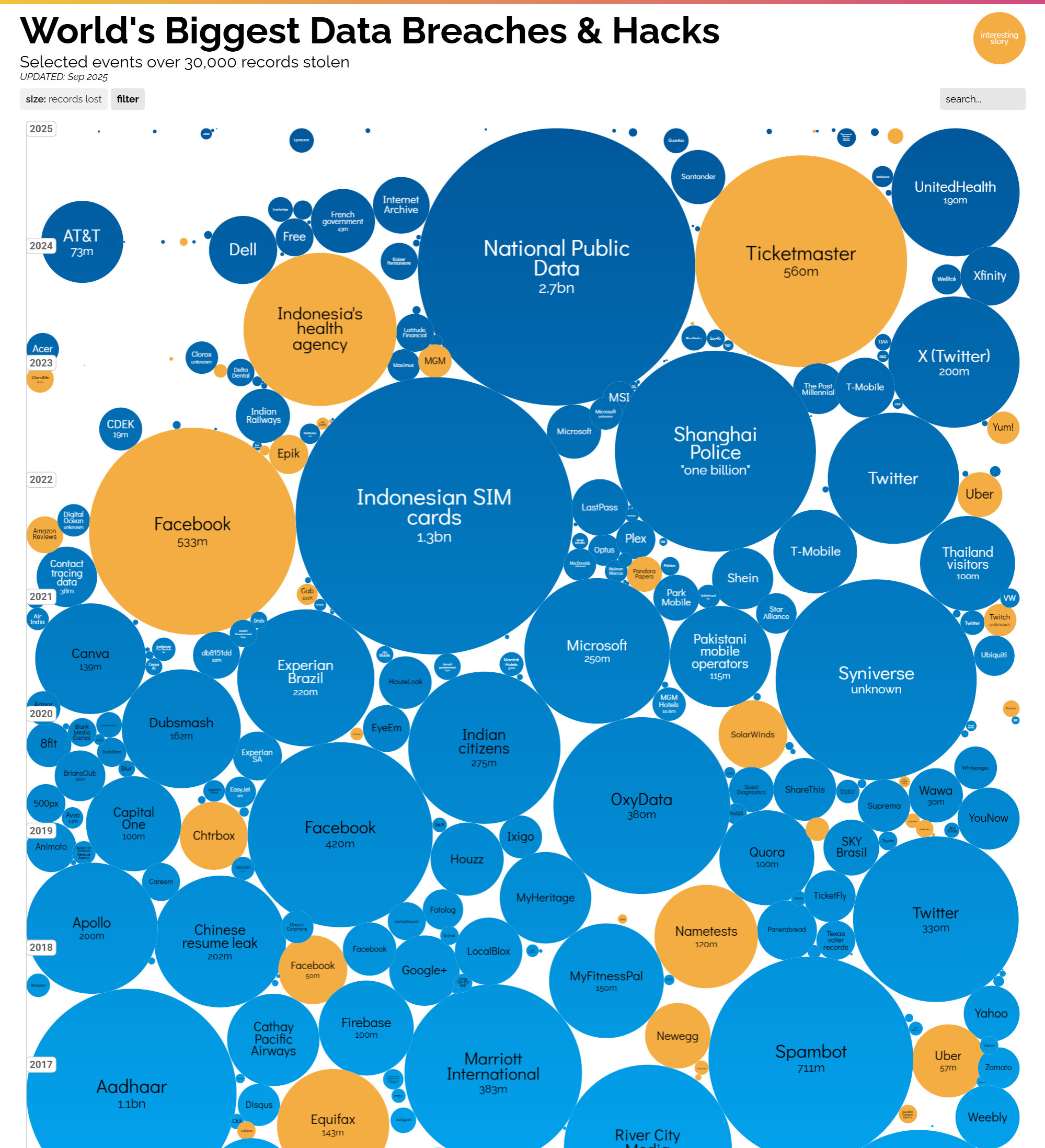
Let’s be honest: these days, cyber attacks on large businesses (and not only large) are totally predictable. One of the recent worrying news: hackers pay employees of large corporations upfront up to £45K (0.5 of Bitcoin) so they can have access to the employee’s account. If the attack is successful, they promise you an additional 15% of the ransom, saying, “you will never need to work again”. This is a true nightmare for every CISO, every SOC operator and every cybersecurity professional who understands the scale and consequences of this. If you want to comprehend the scale of attacks and data breaches, I recommend that you check this web page: World’s Biggest Data Breaches & Hacks. It’s a live chart regularly updated and very “eye-opening”, to say the least.
So, the risks are known, and large companies surely a) understand the risks and b) have money to be prepared. Fun fact: Scattered Lapsus$ Hunters are also linked to high-profile hacks at retailers like Marks & Spencer and Co-op. It seems the lesson was not learned by the industry! Instead, we start handing out taxpayer money to large businesses. I can predict that they will immediately start treating cybersecurity in a much more “relaxed” way. “If things go bad, we’ll pay the ICO fine (if we’re caught, of course). But if things go truly catastrophic, we cry loudly in public, and our government comes, gives us a big hug and covers the fallout. One more thing strikes me: think of the absurdly high ICO fines for data breaches that companies receive after they are hacked. Yet JLR is being offered a safety net that could cost the public sector billions in the long run. Is it fair?
The government might argue that JLR’s failure would ripple across an entire sector that supports hundreds of thousands of jobs. A supply chain collapse could lead to widespread unemployment, reduced GDP, and a hit to Britain’s global reputation as a manufacturing powerhouse. But if we accept this logic, we’re setting a dangerous precedent. This is a truly slippery slope: what about the next company that gets hacked? The next industry that suffers a cyber attack? The government’s role should be to enforce standards and provide guidance - not to act as a safety net for companies that have failed to meet basic security requirements.
Why JLR Should Have Been Better Prepared
The hack was attributed to social engineering - a classic “phishing” or “pretexting” attack that exploited known human vulnerabilities. The attackers also leveraged the JLR’s reliance on external IT partners (Tata Consultancy Services) and a complex supplier ecosystem. If you are in cybersecurity, it’s all well-known.
Where do I see the root of the problem? In my opinion, JLR failed miserably (at least) in these areas:
- Employee training - routine anti-phishing drills can dramatically reduce the likelihood of compromise.
- Regular security testing - routine tests of infrastructure, applications, internal and external networks. From testing individual assets up to running full-blown Red Team exercises. You should do it before the incident to prevent it. Not after!
- Zero-trust architecture - segregating networks so that one single breach doesn’t cascade across the entire business (it’s an “ABC” of the IT and OT security).
- Supply-chain strict security controls - vetting and monitoring third-party access to sensitive IT systems.
All of these are well-known preventive measures. The incident gives reasons to think that JLR simply did not think about it and did not invest enough in cybersecurity. It’s a classic example of “cost of doing nothing”.

(Photo by Lenny Kuhne on Unsplash)
What the Government Could Do
Instead of giving money “on demand”, the government should work on these:
- Mandate minimum cybersecurity standards, including those tailored for critical manufacturing.
- Introduce a National Cyber Reinsurance Scheme - a safety net that encourages companies to invest in risk prevention (rather than rely on government bailout).
- Enforce regular supply-chain security audits - require suppliers to meet certain cybersecurity criteria before they can contract with major OEMs and have them checked regularly.
These measures would shift the burden to companies (where it should be, really), ensuring that cybersecurity is a 100% private business’s responsibility.
The Bottom Line: Prevention Is Always Better Than a Cure
If we want to prevent future incidents like this, we need to make it clear that large companies with deep pockets will spend money on cybersecurity prevention. Yes, it might be a substantial cost, but it is still way cheaper than dealing with a £50 million loss per week. Think of it as an insurance policy: you pay a premium (your cybersecurity investment) to avoid the digital catastrophe. And let’s not forget: the real cost of ignoring security is not just the immediate financial hit but also reputational damage, lost supplier confidence, and the erosion of public trust in industry resilience.
I’d love to hear what you think?
- Do you believe governments should step in when a major company is hacked in the future?
- Should there be stricter regulations mandating cybersecurity investments before firms (especially large ones) can operate at scale?
- Is it possible to ensure that large companies take full responsibility for their security posture?
In the end, the only way to avoid another incident like this is simple: start thinking about cybersecurity in advance. There is always a price. But it’s a price worth paying for the peace of mind that your business is safe from cyber‑attacks, saved jobs and the wheels of business spinning at full speed.