The Price of Neglect. The Big Questions Behind Jaguar Land Rover’s Government £1.5 B Cyber Bailout.
4 October 2025 Reading time: 9 minutes
When a cyber attack stops Britain’s most iconic carmaker, the government steps in with a surprising loan guarantee that would make even the most cautious CFO blush.
The Great British Stall or “JLR on Full Brakes”
Picture this: it’s September 1st 2025, and the Jaguar Land Rover (JLR) production lines have gone silent across Solihull, Wolverhampton, and Halewood. A massive cyberattack - conducted by a gang called Scattered Lapsus$ Hunters has taken JLR’s production lines hostage for almost a month. The result? Roughly £50 million is lost per week, and the whole supply chain is on the brink of bankruptcy.
In the midst of this disaster, we saw a truly unprecedented move: the UK government “pulling a rabbit out of a hat” and rolling out a whopping £1.5 billion loan guarantee to keep the wheels turning. Yes, it sounds like a lifeline for the UK’s iconic carmaker, but it raises a pile of disturbing questions: Why on earth should UK taxpayers chip in for a private company that clearly didn’t pay enough attention to its cybersecurity? Will this set a dangerous precedent, allowing big firms to afford paying even less attention to cybersecurity because now they know the government will help them out? Let’s find out!
The Government’s Spin: “Guys, We Are Protecting Jobs”
It’s the first time a UK company has received financial support specifically because of a cyber incident. But is it an entirely good thing?
Business Secretary Peter Kyle declared that the loan is about safeguarding livelihoods across the West Midlands and beyond. He painted JLR as an exemplary pillar of modern UK manufacturing, supporting over 800,000 jobs nationwide. Fair enough.
Now let’s put our sceptical hats on for a moment. JLR is not a struggling startup, right? It’s a giant business with 34,000 direct UK employees and an enormous supply chain that employs more than 120,000 people. So why does the government feel compelled to guarantee a loan? The answer is twofold:
- Prevent supply chain “ripple effect”: JLR’s 700 suppliers are mostly SMEs. A month of halted production means they’re staring at possible bankruptcy. That’s clearly bad.
- National pride: Jaguar Land Rover is an icon; it’s the “J” in Britain’s automotive DNA.
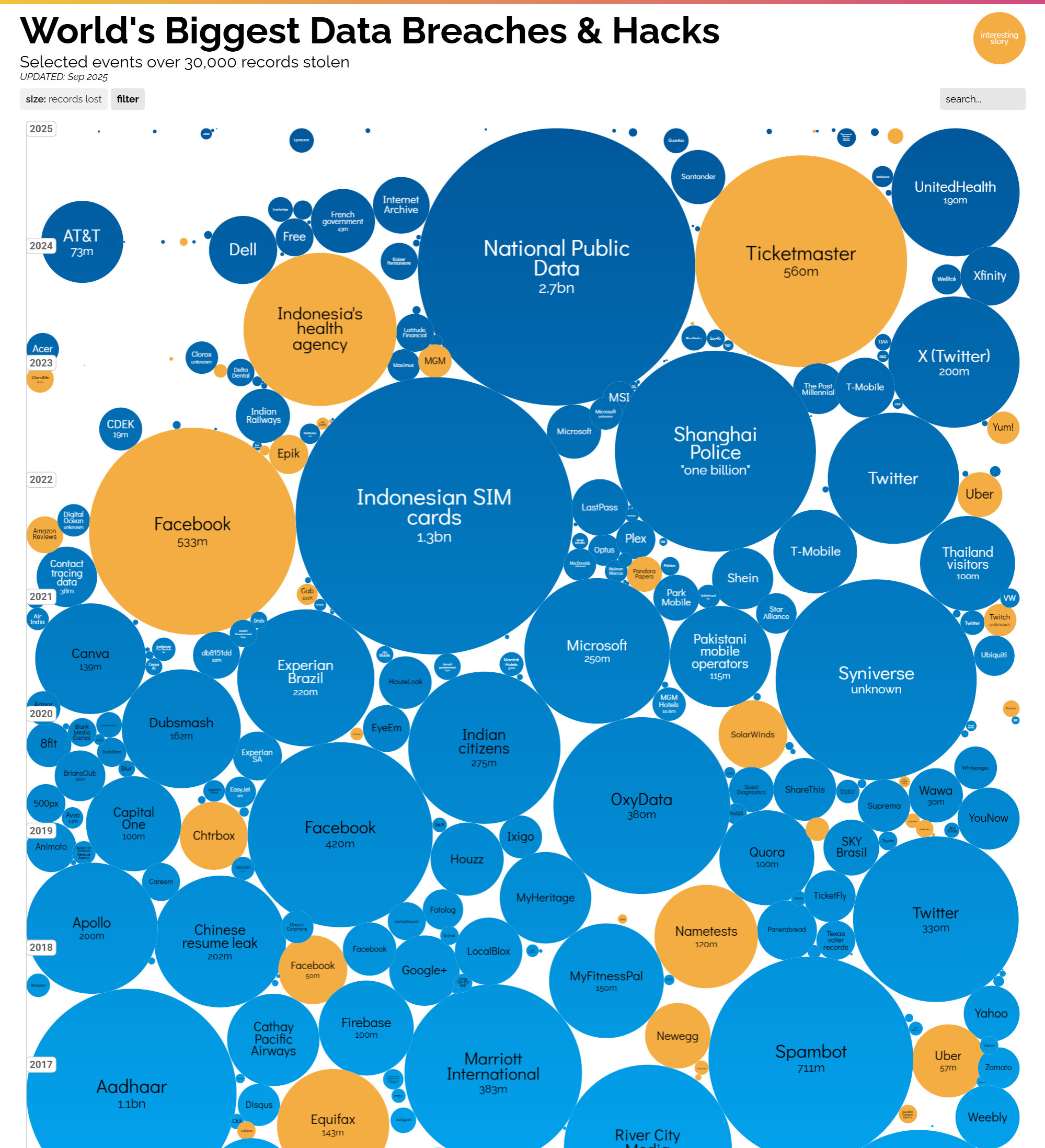
Let’s be honest: these days, cyber attacks on large businesses (and not only large) are totally predictable. One of the recent worrying news: hackers pay employees of large corporations upfront up to £45K (0.5 of Bitcoin) so they can have access to the employee’s account. If the attack is successful, they promise you an additional 15% of the ransom, saying, “you will never need to work again”. This is a true nightmare for every CISO, every SOC operator and every cybersecurity professional who understands the scale and consequences of this. If you want to comprehend the scale of attacks and data breaches, I recommend that you check this web page: World’s Biggest Data Breaches & Hacks. It’s a live chart regularly updated and very “eye-opening”, to say the least.
So, the risks are known, and large companies surely a) understand the risks and b) have money to be prepared. Fun fact: Scattered Lapsus$ Hunters are also linked to high-profile hacks at retailers like Marks & Spencer and Co-op. It seems the lesson was not learned by the industry! Instead, we start handing out taxpayer money to large businesses. I can predict that they will immediately start treating cybersecurity in a much more “relaxed” way. “If things go bad, we’ll pay the ICO fine (if we’re caught, of course). But if things go truly catastrophic, we cry loudly in public, and our government comes, gives us a big hug and covers the fallout. One more thing strikes me: think of the absurdly high ICO fines for data breaches that companies receive after they are hacked. Yet JLR is being offered a safety net that could cost the public sector billions in the long run. Is it fair?
The government might argue that JLR’s failure would ripple across an entire sector that supports hundreds of thousands of jobs. A supply chain collapse could lead to widespread unemployment, reduced GDP, and a hit to Britain’s global reputation as a manufacturing powerhouse. But if we accept this logic, we’re setting a dangerous precedent. This is a truly slippery slope: what about the next company that gets hacked? The next industry that suffers a cyber attack? The government’s role should be to enforce standards and provide guidance - not to act as a safety net for companies that have failed to meet basic security requirements.
Why JLR Should Have Been Better Prepared
The hack was attributed to social engineering - a classic “phishing” or “pretexting” attack that exploited known human vulnerabilities. The attackers also leveraged the JLR’s reliance on external IT partners (Tata Consultancy Services) and a complex supplier ecosystem. If you are in cybersecurity, it’s all well-known.
Where do I see the root of the problem? In my opinion, JLR failed miserably (at least) in these areas:
- Employee training - routine anti-phishing drills can dramatically reduce the likelihood of compromise.
- Regular security testing - routine tests of infrastructure, applications, internal and external networks. From testing individual assets up to running full-blown Red Team exercises. You should do it before the incident to prevent it. Not after!
- Zero-trust architecture - segregating networks so that one single breach doesn’t cascade across the entire business (it’s an “ABC” of the IT and OT security).
- Supply-chain strict security controls - vetting and monitoring third-party access to sensitive IT systems.
All of these are well-known preventive measures. The incident gives reasons to think that JLR simply did not think about it and did not invest enough in cybersecurity. It’s a classic example of “cost of doing nothing”.

(Photo by Lenny Kuhne on Unsplash)
What the Government Could Do
Instead of giving money “on demand”, the government should work on these:
- Mandate minimum cybersecurity standards, including those tailored for critical manufacturing.
- Introduce a National Cyber Reinsurance Scheme - a safety net that encourages companies to invest in risk prevention (rather than rely on government bailout).
- Enforce regular supply-chain security audits - require suppliers to meet certain cybersecurity criteria before they can contract with major OEMs and have them checked regularly.
These measures would shift the burden to companies (where it should be, really), ensuring that cybersecurity is a 100% private business’s responsibility.
The Bottom Line: Prevention Is Always Better Than a Cure
If we want to prevent future incidents like this, we need to make it clear that large companies with deep pockets will spend money on cybersecurity prevention. Yes, it might be a substantial cost, but it is still way cheaper than dealing with a £50 million loss per week. Think of it as an insurance policy: you pay a premium (your cybersecurity investment) to avoid the digital catastrophe. And let’s not forget: the real cost of ignoring security is not just the immediate financial hit but also reputational damage, lost supplier confidence, and the erosion of public trust in industry resilience.
I’d love to hear what you think?
- Do you believe governments should step in when a major company is hacked in the future?
- Should there be stricter regulations mandating cybersecurity investments before firms (especially large ones) can operate at scale?
- Is it possible to ensure that large companies take full responsibility for their security posture?
In the end, the only way to avoid another incident like this is simple: start thinking about cybersecurity in advance. There is always a price. But it’s a price worth paying for the peace of mind that your business is safe from cyber‑attacks, saved jobs and the wheels of business spinning at full speed.

Do Pixels Have Soul: Is AI‑Generated Art Just a Remixing or True Act of Creation?
30 September 2025 Reading time: 13 minutes
Pixels, Passion, and Purpose: The Controversy Over Machine-Made Masterpieces
Imagine scrolling through your favourite feed and stumbling on an image that looks as if it is born from a dream, a swirl of colour that seems to breathe. Your first instinct is often the same as mine: “Wow! That’s… true art!” Yet, beneath every digital brushstroke lies a question that has become louder and louder: Can something created by AI be called art?
As someone proficient with technology, I understand that the AI was trained on thousands of photographs, paintings, and even satellite images. All done by an algorithm. So how could something produced by a machine without intention or emotion or soul be called art?
Today, the answer is no longer a simple yes or no. It has become an ongoing conversation that cuts across museums, studios, cafés, and social media. We have a true flood of AI-generated content - images, music, poems, even entire short films. AI has turned everyone into some sort of “creator”. This is the moment when the famous phrase from “Ratatouille” pops up in my head: “Everyone can cook, but not necessarily everyone should”. This is perfectly applicable to AI-generated content. Yes, these days we can ”create” images or music, literally, with one click. But can we call it a truly creative process? And could we take the liberty to call the outcome “Art”? Let’s discuss this topic together!
Brush, Bot, or Both? Redefining Art in a Digital Age
Art has always been a mirror of human experience. From the ochre-stained walls of Chauvet Cave to the neon graffiti of modern streets, every piece reflects the feelings, ideas, and contexts of its creator. A common definition that scholars and artists alike gravitate toward is, more or less: art is an expression of imagination, skill, or emotion that evokes a response in the observer.
Note that this definition does not hinge on the medium. Stone, canvas, glass, pixels - all can carry beauty, meaning, and emotions. The same holds for tools: from chisels to brushes, then laser cutters and now neural networks. What has also changed is the relationship between creator and medium. In the past, a painter had to translate emotion into pigment. In the present, an artist may feed a prompt into an LLM model that then renders an image that might (or might not) align with the artist’s intention.
Consider this: a child drawing with crayons is arguably producing art even if the result is “messy.” The crayon is merely a tool. Likewise, a smartphone camera is just another instrument in the artistic toolkit - one that democratises access to photography but does not automatically guarantee aesthetic value. Thus, AI too can be viewed as an advanced tool: one that extends our reach and offers new possibilities in return.
Another example: imagine a composer who writes a symphony for an orchestra and then hands it over to a robot to perform. The music remains their creation; the performance becomes a collaboration with technology. Once again: AI is a tool that extends our expressive range rather than a rival to human creativity.

© Aleksander Gorkowienko 2025
The Soul Debate: Does Intent Matter?
The phrase “it has no soul” is a shorthand for a much deeper scepticism: If a machine cannot feel, how can its output carry the essence of art? This objection rests on a particular “accepted model” of the human soul - its capacity for intention, suffering, and self-reflection. We blindly accept that music, an oil painting, or a photograph can “possess soul” because it’s made by a [soul-carrying] creative human. But is it true? The “soul” of any art lies in its ability to stir emotions, provoke thought, or inspire action. It's about the experience it creates!
Artists and technologists alike have argued that intent is mediated by human agency. When a prompt engineer writes: “paint me a melancholic forest at dusk,” they are infusing the request with intention. The AI merely translates that intent into pixels, guided by patterns learned from millions of images. In this sense, the machine is an extension of the artist’s imagination, not its replacement.
Take, for example, the work of Refik Anadol. His installation “Artificial Realities” uses machine learning to transform vast datasets of coral images into immersive visual experiences that raise awareness about climate change. Anadol himself does not claim to have authored every detail; he curates data, designs parameters, and interprets outputs. The soul of the piece is still rooted in his vision for environmental activism, despite the fact that the image is created by AI.
Art as a Human Endeavour: Skill, Creativity, Imagination - now applied to AI
The definition of art that many scholars endorse - art as an endeavour that uses skill, creativity, or imagination to express emotions or ideas - is inherently human. Yet the skill required to create AI art is different from that of a traditional painter. It is not brushwork but prompting: the ability to translate thought into language that AI can understand.
This shift does not diminish the value of human skill; rather, it redefines what counts as artistic proficiency. Imagine a future where an artist’s imagination is directly translated into visual or sonic output through neural interfaces. The creative act may become more about conceptualising ideas than mastering brush strokes. In such a scenario, imagination could indeed eclipse traditional design skills.
I think the conversation should not be framed as “AI art versus human art.” Instead, it is more productive to view AI as a collaborative partner. The new “AI chisel” offers surprising combinations of styles and access to datasets beyond any single artist’s reach. But it’s human who brings emotions, context, narrative, and ethical considerations - elements that the machine cannot yet generate independently.

© Aleksander Gorkowienko 2025
Creative Tools Across Time: From Paintbrush and Chisel to Camera, Photoshop and AI
Photography itself is a compelling precedent for this discussion. In the early 20th century, photographers like Ansel Adams or Henri Cartier-Bresson were celebrated not merely for their technical mastery of film but for their ability to capture emotional truth through composition and timing. Today, almost everyone carries a smartphone capable of taking high-resolution photos. Yet the vast majority produce images that are fleeting snapshots rather than considered works of art.
The same logic applies to AI. While the technology is accessible, the artistry lies in how it is employed - in choosing datasets, training LLMs, designing prompts, and selecting which outputs resonate with a particular narrative or aesthetic. The democratisation of tools does not automatically equal the democratisation of art; instead, it expands the potential for creative expression.
Modern cinematography further illustrates this point. Films (and especially blockbusters) seamlessly blend hand-crafted sets with CGI to create immersive worlds that feel both tangible and fantastical. The audience is rarely aware of the digital scaffolding; what matters is the emotional journey crafted by the director, cinematographer, and visual effects team.
Examples That Sparked Conversations. An Art or not?
DeepDream: The Dream Within a Machine

Image created with DeepDream (Source: Wikimedia Commons)
Google’s DeepDream was one of the first publicly visible AI art projects. By feeding an image into a convolutional neural network and then amplifying patterns that the model recognised as “interesting,” DeepDream produced hallucinogenic visuals - a blend of reality and algorithmic imagination. I vividly remember when it prompted long philosophical debates about whether these images were mere visual noise or a new form of artistic expression.
Refik Anadol’s Artificial Realities

Refik Anadol: Artificial Realities Coral - A (shop.serpentinegalleries.org)
Anadol’s work with coral data sets showcases how AI can transform scientific information into aesthetic experiences. By mapping complex biological patterns onto spatial audio-visual installations, he tries to bridge the gap between art and environmental science, inviting viewers to confront ecological issues through amazing sensory immersion.
Sofia Crespo’s Neural Zoo

Courtesy of Sofia Crespo
Argentinian artist Sofia Crespo uses AI to create new (let me call them: “speculative”) life forms in her “Neural Zoo” project. She feeds images of real animals into generative models, then manipulates outputs to generate fantastical creatures that challenge our perceptions of nature and evolution.
The Future of Artists: Displacement or Collaboration?
There is legitimate concern that AI could displace traditional artists by automating tasks like colour grading, texture generation, or even composition. Yet history suggests that new tools rarely render professions obsolete; new tools transform them. As the “digital brush” becomes more sophisticated, artists may find themselves reallocating time from routine tasks to higher-level conceptual work - crafting narratives, curating datasets, and engaging audiences in dialogues about meaning.
Here comes one fundamental difference of AI-driven artistic process: unlike a traditional tool that merely follows commands, many modern AIs engage creators. They can ask clarifying questions, offer variations, or even propose unexpected directions based on the prompt. It’s something entirely new: a true dialogue between artists and their tool. Maybe I go too far, but to me it's almost like a conversation between an artist and his muse - only now the muse is code!
Imagine a future where a neural interface reads our visual cortex and translates thoughts directly into images. Would that still be art? The answer depends on how we define creativity. If the image is a faithful rendering of an internal vision, then perhaps the act is more akin to memory capture than artistic creation. However, if the interface introduces novel transformations - mixing styles, layering emotions - it could become a powerful medium for self-expression and creating something truly unique.
In either case, the artist is us: we decide what to imagine, how to interpret it, and why we share it.

© Aleksander Gorkowienko 2025
The Beauty of Subjectivity
Ultimately, beauty is in the eye - and mind - of the beholder. A piece that moves one person may leave another untouched. This subjectivity remains whether the work of art was hand-painted or machine-generated. Each image created by AI we encounter today carries a lineage: from the data it was trained on through the prompt that shaped it, to the viewer’s own experiences.
The proliferation of AI art forces us to confront one more time a fundamental truth about creativity: It is not bound by tools but bounded by intention and interpretation.
AI-generated art is neither a threat nor a salvation; it is a new frontier in human expression. It expands our palette, invites collaboration across disciplines, and challenges long-held notions of authorship and authenticity. Rather than fearing displacement, we should view AI as an ally - an instrument that amplifies the human imagination.
So, what does this mean for you?
If you’re a writer, think about how prompts can help you generate visual narratives. If you’re a painter, consider training models on your own work to explore variations you might not have imagined! It might help you to express your feelings and ideas better! And if you’re simply an AI art enthusiast, remember that every click and scroll is part of a larger conversation about what art means in the 21st century.
…and what is your experience?
What’s your experience with AI-generated art? Have you tried creating a piece yourself? If you found this article thought-provoking, share it and spread the dialogue further. Together, we can shape the future of art - one prompt at a time.

Your Router Is Watching You: The Dark Side of Wi-Fi Sensing Technology
4 September 2025 Reading time: 7 minutes
Have you ever wondered whether your humble Wi-Fi router could, by any chance, tell you who entered your living room, when they moved or even what they were doing? That question is no longer theoretical. It all becomes a reality thanks to the Wi-Fi Sensing technology. While the idea sounds like something out of science fiction, many of today’s routers are already capable of turning into motion detectors and more.
How does the magic work?
At its core, Wi-Fi Sensing relies on beamforming technology: a clever method employed by the majority of modern routers that enables them to focus their signals on specific devices while communicating with them. We are talking about routers equipped with multiple antennas and capable of supporting at least the 802.11ac version (also referred to as “Wi-Fi Five”). Beamforming generally results in faster and stronger signal quality, which we've all come to rely on when browsing the Internet, streaming our favourite movies or playing online games. But this is only a part of the story.
In our modern houses, every device - your smart speaker, TV or printer - is quietly and constantly emitting radio waves. When these signals bounce off objects and people, they change subtly. Modern routers equipped with beamforming focus their antennas to maximise signal strength towards each device, constantly measuring the Channel State Information (CSI) - the amplitude and phase of the transmitted radio waves.
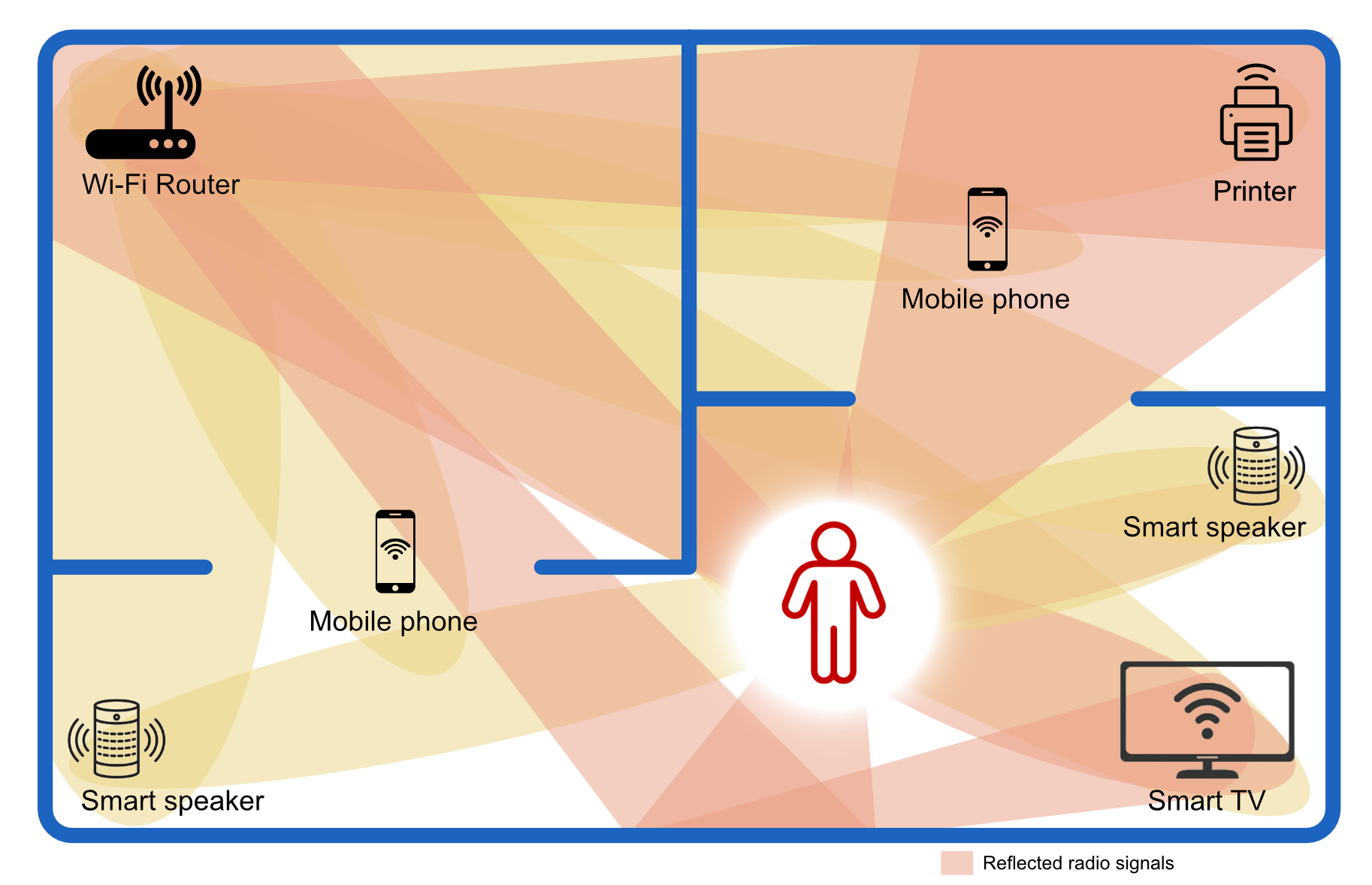
When a person walks between the router and one of its connected devices, that human body introduces tiny changes in the pattern of radio waves. The router detects these deviations as shifts in CSI. By feeding those patterns to machine learning algorithms, it is possible to recognise movement, detect an intrusion, or even infer specific actions such as standing up or waving a hand. All this happens at the very edge of the network - inside the router itself - so no extra hardware is required beyond what most households already have. What begins with just detecting motion eventually becomes a highly accurate system that can tell where you are at different times of day, in which particular room, and how many people were with you. Wi-Fi Sensing is capable of detecting with high accuracy (and leaking!) users’ personal characteristics such as height, weight, or gender, thereby breaching privacy regulatory frameworks.
Implications
Many could welcome Wi-Fi sensing into their lives for its convenience, as “yet another smart home feature” like lights could be switched on when a user walks through the door and have them to automatically switch off once they leave. What's not to like: you have a home surveillance system for free.
However, as it stands now, users are unaware that these new innovations can easily introduce security threats to their very own homes. When used by malicious individuals or exploited, Wi-Fi sensing can be misused and pose as a serious threat to personal or corporate security and privacy, exposing even the most seemingly secure of living environments.
Not only can homeowners monitor who comes and goes. Vendors can easily share the collected motion or presence-related data with police or other “third parties” on demand. The collected information can also be sold or stolen, revealing the life patterns of thousands of homeowners.
We should not forget that home routers are already frequent targets for hackers who either eavesdrop on users or profit from the collected data in various ways. Nothing stops malicious actors from “mining” motion sensor data and, e.g. selling those insights to burglars or “whoever pays”.
Fun fact: it might be interesting to know that IEEE 802.11bf standard will be ready to formally standardise Wi Fi sensing in 2025. The amendment adds MAC and PHY layers features that enable robust sensing in both sub 7 GHz bands and frequencies above 45 GHz. When published, 802.11bf provides a unified framework for presence detection, recognition of human activities, and monitoring the environment by using existing Wi Fi infrastructure. So there will be more Wi-Fi Sensing everywhere, and we all have to understand well the security implications of this technology.
Can We Protect Ourselves?
Protecting yourself against these types of vulnerabilities is more crucial than you think. You have no influence on anything that happens on the vendor’s side, but you certainly have control over what happens in your home or office. Because Wi-Fi sensing relies on the standard wireless signals that already fill our environment, it’s nearly impossible to block it entirely. However, you can still reduce its potential dangers by shielding critical spaces from the wireless signals. In highly sensitive areas, such as research labs or conference rooms, take care to block Wi-Fi entirely. Proper signal shielding will neutralise attacks that depend on Wi Fi Sensing. If you want to go one step further, consider installing structural barriers such as Faraday cages or using materials that absorb or reflect radio waves, or otherwise preventing the signals from leaking into or out of those spaces.
Don’t forget about the elements of standard cyber hygiene. Make sure all Wi-Fi-enabled smart devices within your network are properly patched, their software up-to-date, and that a strict WPA2 or WPA3 security is in place. If possible, avoid sharing passwords with people outside of your “circle of trust” (personal or corporate) who, sometimes, have little understanding of security. Using guest Wi-Fi passwords with expiration time could be a good idea. One more thing that is worth remembering: think twice before introducing a new device to your home or corporate Wi-Fi network, especially if the vendor is, let’s call it “questionable”. I would also strongly recommend avoiding registrations with the vendor’s cloud services, unless it is absolutely necessary and you understand all the implications. If you have no choice and must register, use a disposable email address for registration and do not provide any of your personal details (yes, I am talking about security cameras, cleaning robots, etc.).
Finally, always stay proactive: monitor your network for anomalies, keep up to date with emerging risks, and remember that having even the simple measures in place, like regular updates, strong keys, and cautious onboarding, is better than doing nothing.
More Information
- A large collection of Wi-Fi Sensing Resources (https://www.wifisensing.io)
- ESPARGOS is a very large dataset (~120 GB https://espargos.net) available if you want to conduct your own research. The dataset was created with a phase-locked antenna array and allows studying spatial problems such as positioning, segmentation and phase effects.

The AI Hiring Bot Has Millions of Sensitive Data Records Exposed
10 July 2025 Reading time: 5 minutes
TL;DR: Multiple vulnerabilities found in McDonald's AI-powered hiring system exposed data of 64 million job applicants. Security issues, such as weak passwords and a lack of robust security design, leave sensitive information exposed in the wild. This exercise is (one more) wake-up call for companies to reassess their reliance on automated systems and take concrete steps to protect sensitive information. [Source].
Cybersecurity is never limited to just IT systems but extends to all corporate environments. This story is about hacking an automated AI-driven hiring mechanism. Imagine a scenario where you apply for a job online only to find your sensitive personal data - name, email address and phone number - being shared without your consent on the dark web. Sounds far-fetched? Unfortunately not. The recent exercise shows that 64 million applicants' personal data records in McDonald's AI hiring system, McHire, could have been easily compromised.
Not-So-Tasty Recruitment System
Security researchers Ian Carroll and Sam Curry found that the McDonald's McHire platform, developed by AI software company Paradox.ai, had numerous (basic!) security vulnerabilities, enabling hackers to breach the applicant database with a simple administrator password like "123456." After gaining access to the McHire system, security researchers uncovered an Insecure Direct Object Reference (IDOR) vulnerability within the applicant database. By enumerating the applicant ID, they were able to access all the database records. This flaw enabled access to a massive amount of sensitive personal information, including names, email addresses, phone numbers, and chat logs spanning several years. Needless to say, the accessed data in the wrong hands could be easily exploited for phishing, fraud, or other malicious activities. Both McDonald’s and Paradox.ai recognised the gravity of exposing sensitive applicant data and the critical nature of the incident. McDonald's expressed disappointment regarding the security lapses of its third-party vendor, but would it change much?
How on Earth is This Possible?
The answer lies in a well-known security flaw: a weak username and password combination as simple as the immortal "123456". The researchers discovered these vulnerabilities by using a trivial dictionary attack - a "traditional" and basic technique where an attacker uses words and common patterns to identify weak passwords. Success after 30 minutes - not bad!
Reading between the lines, the ease of this breach might suggest deeper issues in the platform’s development process, potentially stemming from an over-reliance on AI-driven code generation. It’s plausible to assume that the security flaws emerged due to automated programming tools producing insecure code. In an AI-driven development environment, algorithms may prioritise functionality and speed over security, inadvertently embedding multiple vulnerabilities if not rigorously checked. The lack of robust human control and supervision in the SDLC could have led to a failure to enforce the necessary secure coding standards.
Recommendations? Elementary, my dear Watson.
How do we protect ourselves from falling victim to such security threats? The answer lies in taking simple, very well-known, yet effective measures to safeguard our businesses.
To prevent cybersecurity issues, organisations should enforce strong password policies with complex, lengthy passwords and multi-factor authentication. It is important to secure access to all sensitive resources (especially databases) with role-based access control. It is important not to forget about running regular security audits: conducting penetration testing (PT), automated vulnerability scans (VA), and engaging third-party security firms - it will tremendously help to identify weaknesses at the early (development) stages. And please always remember about employee training on secure practices and phishing awareness. The training can work best if combined with an existing robust incident response plan that ensures quick action during breaches.
Separate words should be said about having a secure software development lifecycle (SDLC) in place, as it integrates security practices at every stage of software development: from design to deployment. By incorporating threat modelling, secure coding standards, and regular security testing, it is possible to substantially reduce the risk of exploitable flaws much earlier (and cheaper).
So we, humans, are still needed! To me, this all highlights the necessity of integrating human expertise into modern "AI-assisted software development". Otherwise, we will have more opportunities to log in with "123456" to mission-critical systems and see more catastrophic breaches that expose sensitive data.

Cyber Attacks Becoming a Nightmare for UK Businesses. Are CEOs And CISOs Playing a Cybersecurity Roulette?
30 June 2025 Reading time: 10 minutes
Each passing day brings a new wave of cyber threats that loom over the future of business, waiting to strike at the most unfortunate moment. I was scrolling through today’s article in The Guardian, thinking “Ah, same old, same old”. But let us all stop for a moment and try to think together about what is really happening and how to break the vicious circle.
According to the UK Cyber Crime Statistics in 2025, over 560000 new cyber threats are discovered daily. Do you want more numbers? Recent figures released by the Royal Institution of Chartered Surveyors (RICS) show that an alarming one in four UK companies have suffered at the hands of cyber-attacks within just the last year alone. The predominant majority (81%) of those UK businesses that suffer from a Cyber Security Attack are small and medium-sized businesses (SMBs/SMEs). It is essential to grasp the extent of these statistics and their potentially catastrophic implications on a business's survival and reputation.
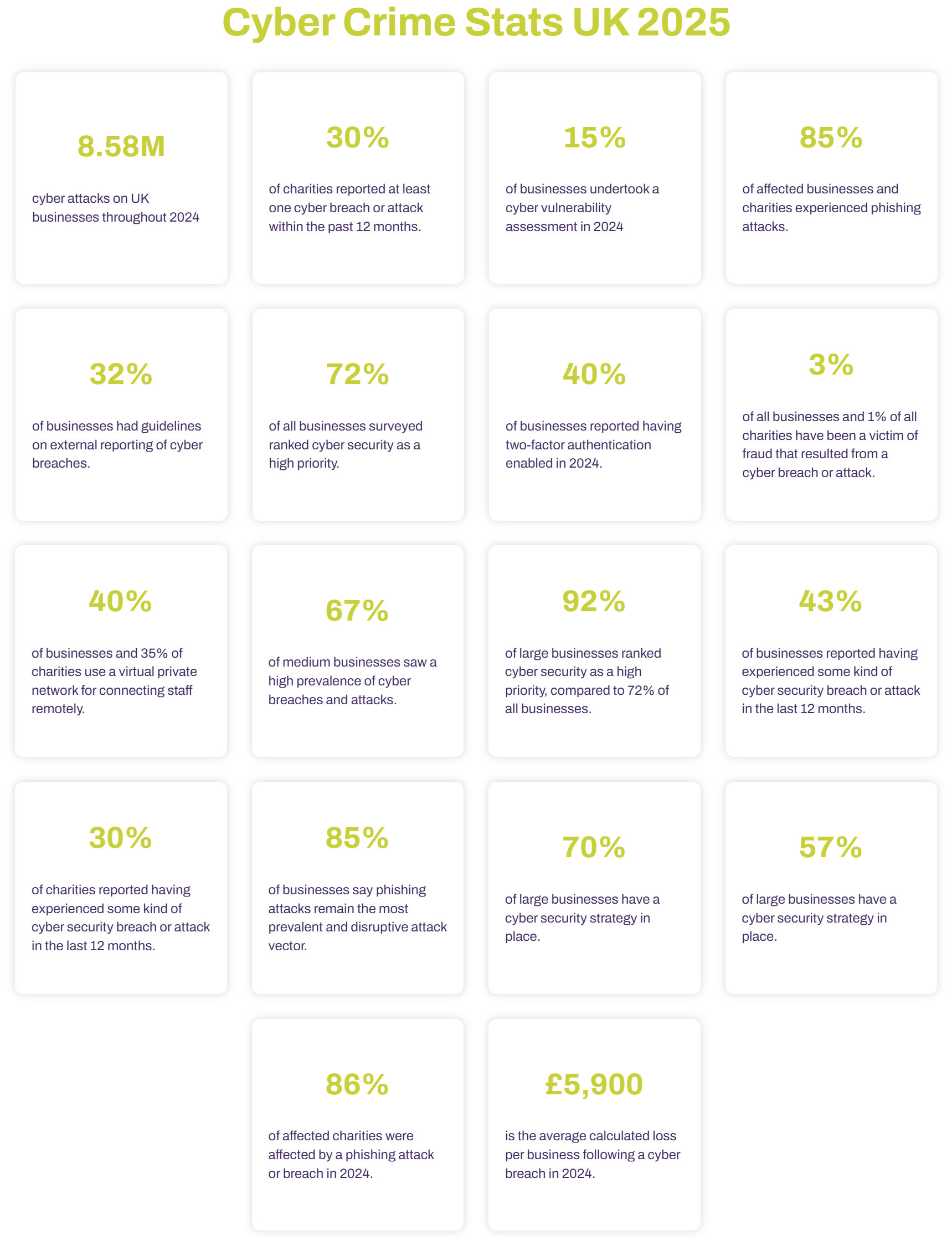
(Source: www.twenty-four.it/services/cyber-security-services/cyber-crime-prevention/cyber-crime-statistics-uk)
What lies at the heart of this growing crisis? Complacency, lack of awareness and absence of a long-term security strategy among some CEOs and CISOs are major contributing factors. Despite being aware of the looming dangers, they appear to “underestimate the enemy” and rather think about the short-term, small “demonstrable wins” (because it looks good in reports, right?), but at the same time, putting their entire companies at risk. This was exemplified by a recent high-profile attack on Marks & Spencer, which suffered weeks of downtime due to a catastrophic cyber breach that, in turn, led to a colossal financial loss. This all looks like a perilous game of cybersecurity roulette, and I am not sure if businesses can afford to play.
There is an opinion that these days, traditional antivirus software is largely useless in preventing the newer agile forms of attacks. So, can we still protect our precious business? The answer lies in taking multiple proactive measures to safeguard against modern, rapidly changing cyber threats. By implementing a series of basic yet crucial measures, businesses can significantly reduce their risks. These include regular software updates and system checks, comprehensive training programs for employees to identify potential scams, educating staff about the benefits and risks of new technologies, and ensuring that every employee is equipped with the necessary knowledge and skills to navigate this complex digital world. Do not forget to employ multiple authentication methods for enhanced security, conduct routine system checks and do prompt software upgrades, and you will put your business in a much better position.
I think it's a good “wake-up call” for leaders across all sectors to reassess their security protocols and take swift action. We must take immediate action - the costs and potential brand damage could become too high a price to pay in future. Do not wait until your business's vulnerabilities are exposed by hackers. Instead, implement basic cybersecurity measures today (and don't forget to ask professionals to come and revalidate them!).

Cybersecurity: A Big Guide for Small Businesses
20 June 2025 Reading time: 12 minutes
Every day we see that the threat landscape continues to evolve at breakneck speed, but one could be surprised by discovering that not only large enterprises, but small and medium-sized organisations have become prime targets for cybercriminals. But why? In many cases, it is a simple case of a lack of awareness leading to underinvestment in cybersecurity measures. While large corporations may have the budget to invest in cutting-edge technology, SMEs often struggle to keep up.
So, how can small businesses protect themselves without breaking the bank? Ultimately, the key to surviving lies not in luck but in preparedness.
One of the most effective ways for small businesses to fortify their cyber defences is by empowering employees with essential cybersecurity knowledge. Equipping your staff with the right skills to identify and combat online threats can prove invaluable in the fight against “daily” cyber threats.
In addition to employee education, it is important to regularly check software updates and patches, as those can close known vulnerabilities before they can be exploited by malicious actors. This simple yet effective measure can significantly reduce the risk of falling prey to cyberattacks.
It's surprising that despite its importance, many organisations still forget about some basic cyber hygiene, such as password security. A staggering 81% of hacking-related breaches are attributed to weak or stolen passwords. Addressing this issue forthwith is crucial and, ideally, combined with two-factor authentication mechanisms (2FA) in place.
Another critical aspect of cybersecurity that cannot be overlooked is the establishment of reliable backup systems. Not only does this safeguard against accidental data loss in the event of a ransomware attack, but it also saves precious time and money that would have otherwise been spent on (very) costly recovery. By the way, do you have an Incident Response Plan? When was the last time you had it tested?
There are many cybersecurity tools and resources which could be used for free. Local chambers of commerce, small business associations, or online communities often provide various free workshops, mentorship, or networking events. Government programs or grants for small businesses can also offer financial relief for investment in cybersecurity. Your employees can learn how to use free tools and successfully maintain the cybersecurity baseline themselves.
Last but not least, you might be surprised, but hiring professional penetration testing teams also doesn’t have to be expensive. Some cybersecurity firms, such as Risk Crew, offer services tailored for small and medium-sized enterprises (SMEs), balancing quality and affordability. These solutions will test your systems for vulnerabilities, ensuring robust protection without the high costs typically associated with enterprise-level services.
So, what can you do to get started today? By incorporating one step each week into your cybersecurity routine and monitoring its progress, you'll be on your way to building a robust defence against modern cyber threats. Always remember that cybersecurity is not just an IT problem; it's a team effort that requires every employee to be engaged. By focusing on high-impact, low-cost strategies, small businesses can significantly reduce their risk of cyberattacks and become a tough nut to crack for hackers.